Authentication in Aeneis via Spring Security
Token-based authentication allows user data to be synchronized with Aeneis via the Spring Security framework. Users can therefore access the Aeneis portal directly via single sign-on (SSO).
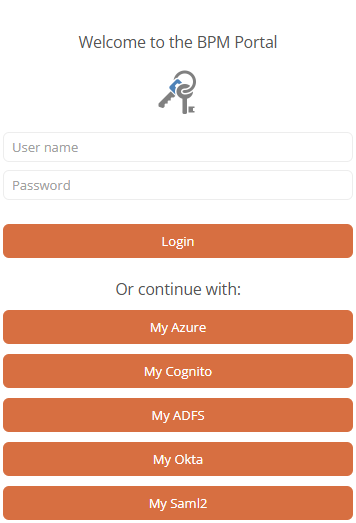
In the ServerAdministration, you can configure token-based authentication for databases via multiple providers. Once token-based authentication has been configured, users can select their preferred authentication method when logging in to the Portal.
Important notes:
-
If token-based authentication is set up, users must initially select their preferred authentication method via the Portal login dialog. By default, the database login is also available to users via the user name and password.
Note: You can deactivate the login with user name and password via the Portal report registration.
-
The selected authentication method is saved for 30 days, so that a new selection is only necessary after this period.
-
The display name of the respective login button can be determined via the configuration of the authentication method.
-
The authentication in Aeneis via Spring Security works without an additional LDAP Sync license.
Functions:
-
Create authentications via the providers Azure AD, AWS, ADFS, Okta and SAML2.
-
Make subsequent changes to the respective authentication in ServerAdministration at any time, e.g. to adjust the client secret or the display name of the button when logging in to the Portal.
-
Automatic creation of users and synchronization of the configured group assignments when accessing the Portal for the first time
-
Transfer of names, e-mail addresses and groups from the directory
Note: If a user is removed from the directory after synchronization, he/she remains present in Aeneis. However, access is not possible because no valid token is created by the identity provider.
Preparations:
-
Existing users must use the user ID that is used and synchronized within token authentication. If different IDs are used, additional users are created as part of the automatic creation process.
-
The SSL trustkeystore is always "aeneis-server-keystore.jks" as of Aeneis 6.3.SR1.
-
SSL certificates: The public certificate of the login page of e.g. Azure must be added to the application directory. If there is an error due to a missing certificate, it must be added in the application directory under "aeneis-server-keystore.jks". For Azure, for example, the certificate "stamp2-login-microsoftonline-com.pem".
Limitations:
-
Token-based authentication can only be used in the Portal.
-
The electronic signature (property Show login dialogproperty in transitions) only works with ADFS and Azure. If authentication via ADFS SAML2 is configured, only the application.yml file needs to be modified for this, see Electronic Signature for SAML2 ADFS .
-
The synchronization of the groups only works via Azure, ADFS, and SAML2.
Automatic user import
To automatically import users that are synchronized via token-based authentication, activate the Automatic user import property in the properties of the database object in the SystemAdministration:
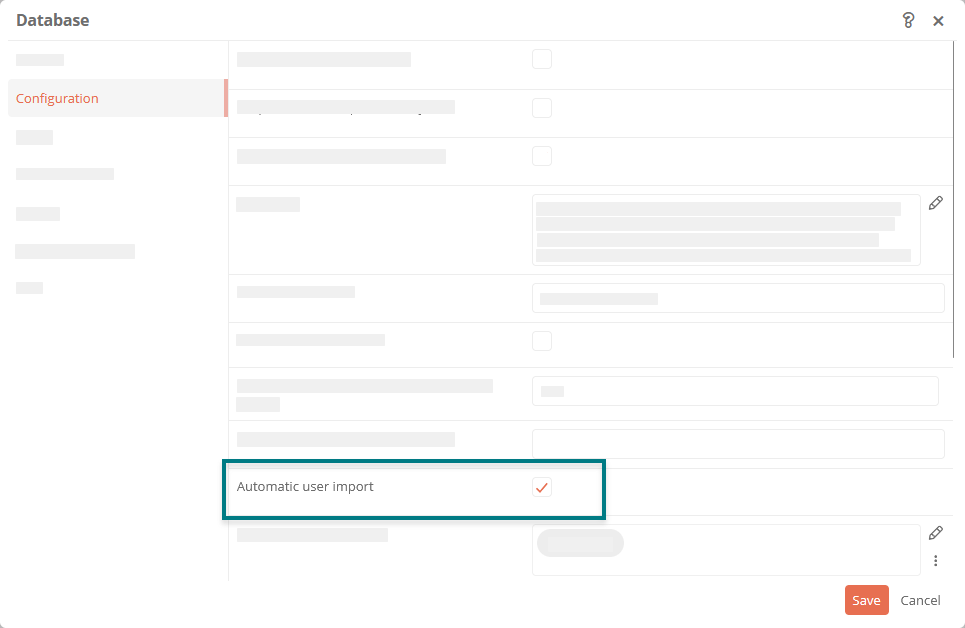
Note: With ADFS and Azure, the UPN (User Principal Name) is used as the ID for the automatic user import. The username is used with AWS.
Automatically update users
To automatically update users who are synchronized via token-based authentication and who change, activate the Automatically update imported users property in the properties of the database object in the SystemAdministration:
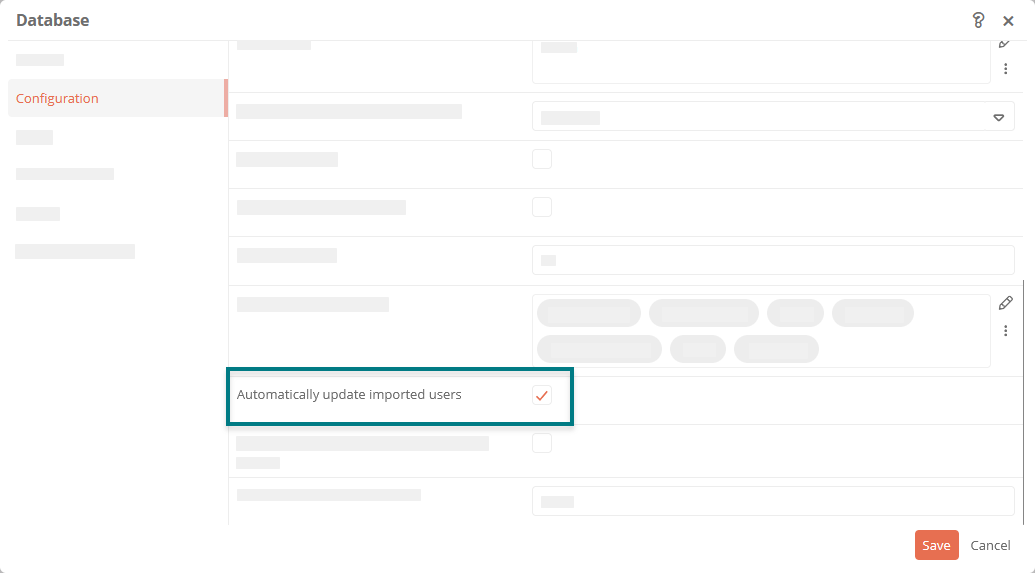
The following attributes are updated as soon as users log in:
-
User name
-
User email
-
User groups: If groups are added in the Groups attribute for LDAP registration, then the user will be added to these groups at the next login. If a group is removed from the Groups attribute for LDAP registration, then the user is not automatically removed from the group, but must be removed manually.
Log in to the Portal
Once authentication has been set up in Aeneis via SSO, users log in via the corresponding SSO button in the Portal login dialog.
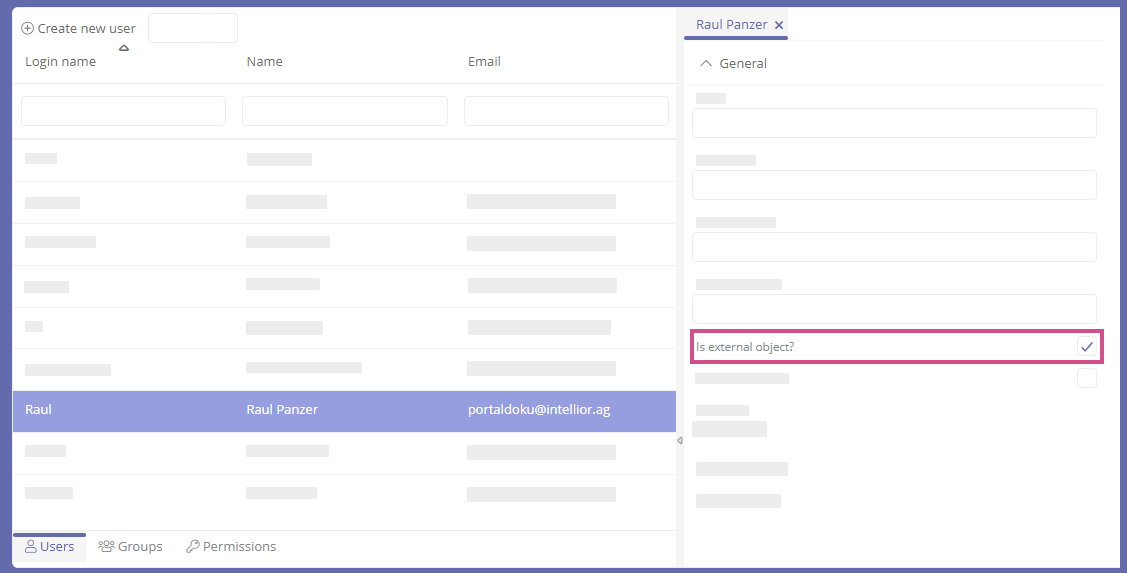
Users that have been automatically imported into Aeneis via the interface have the property Is external object? If users were already created in Aeneis and SSO is subsequently activated, the property Is external object? must be set manually. The property Is external object? enables users to log in to Aeneis only through the token based authentication that has been set up.
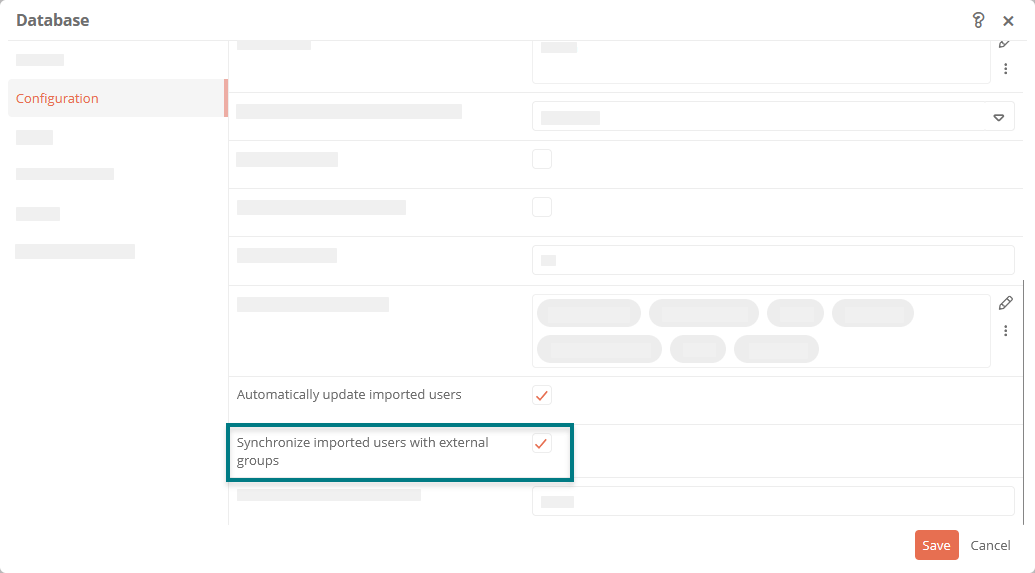
Synchronize users and groups
To synchronize imported users with external groups, you can activate the Synchronize imported users with external groups property in the properties of the database object in the SystemAdministration.
Requirements: For correct synchronization, the transmission of the groups in the token must be configured in the IDP. The ID of the group must match the value of the group that is transferred in the token (in ADFS TokenGroups - unqualified name, in Azure samAccountName). In Aeneis, the property Is external object? must additionally be activated in the group and the property External synchronization ID must be empty.